How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

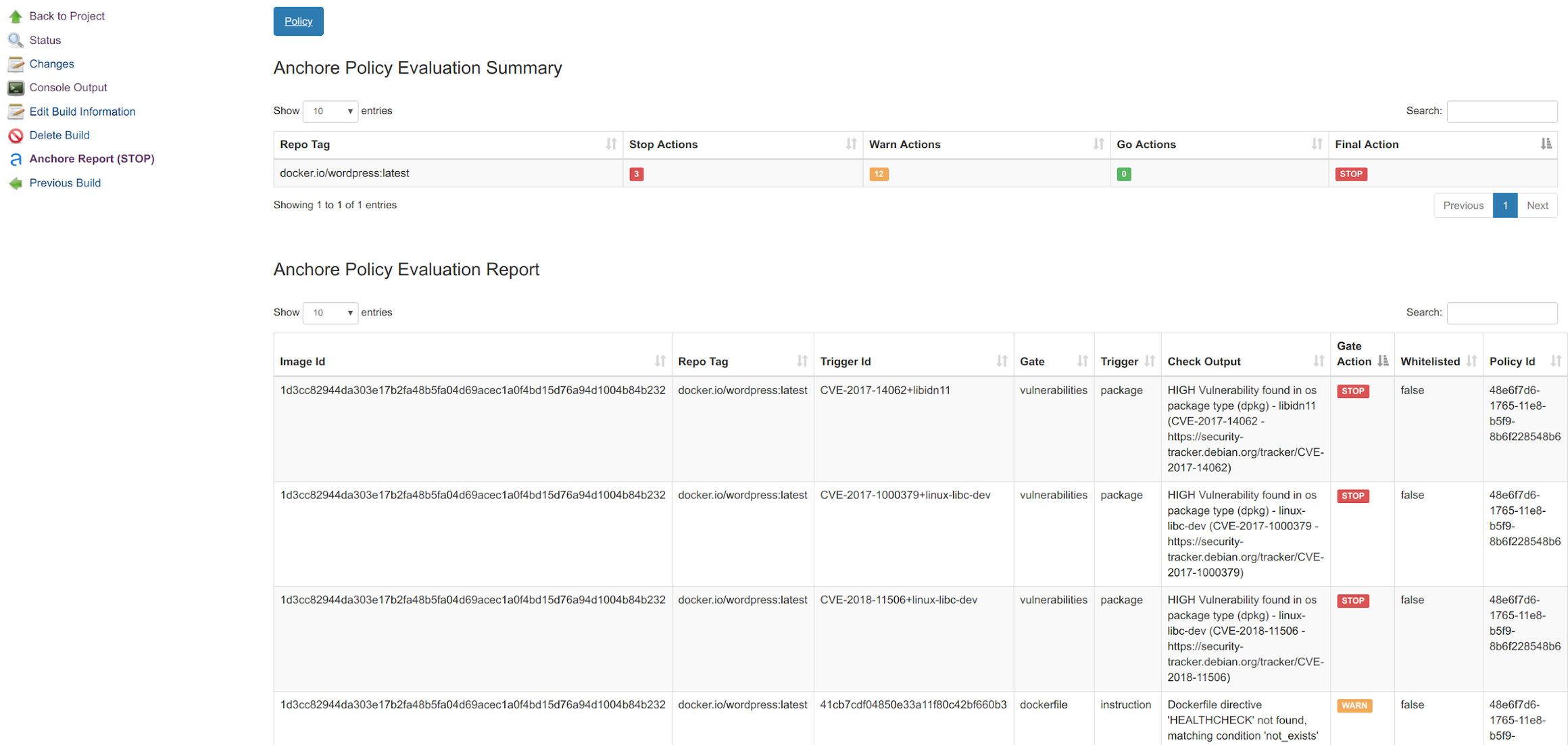
How to scan vulnerabilities for Docker container images — Part2 | by Luke Skywalker | System Weakness
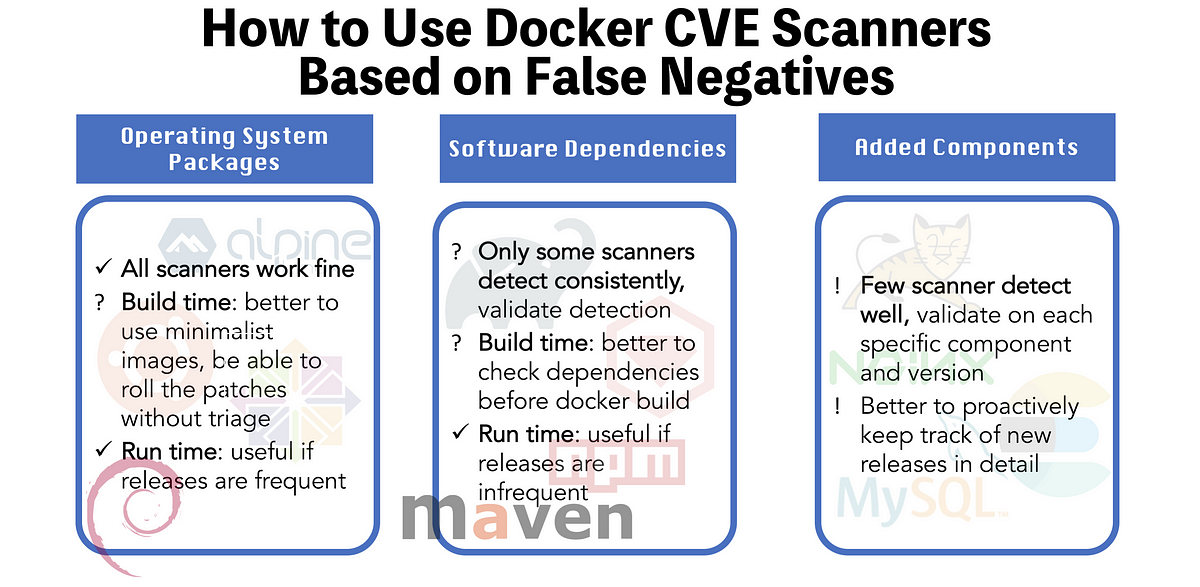
Testing Docker CVE Scanners. Part 3: Test It Yourself/Conclusions | by Gabor Matuz | The Startup | Medium

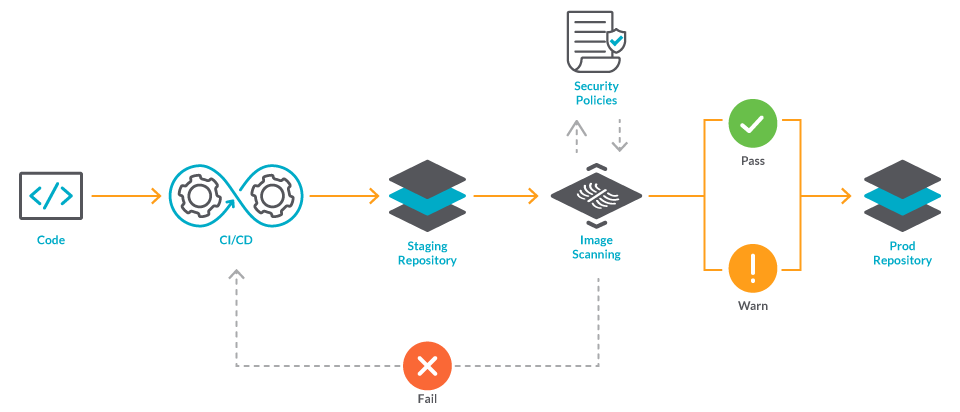
Adding Image Security Scanning to a CI/CD pipeline | by Larbi Youcef Mohamed Reda | alter way | Medium